By Julian Arias BeltranAs you probably know, Microsoft has changed its certification program. This can be quite confusing so we hope this blog gives you the answers and advice you need in order to know which exam to take next. Choosing the right exam now, will help you get your next certifications faster.
By Julian Arias BeltranAs you probably know, Microsoft has changed its certification program. This can be quite confusing so we hope this blog gives you the answers and advice you need in order to know which exam to take next. Choosing the right exam now, will help you get your next certifications faster.
Where to start your certification path?
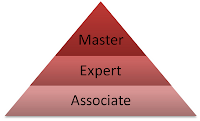 Microsoft has made their certification paths into a pyramid:
Microsoft has made their certification paths into a pyramid:As you can see, it has been divided into three parts. You start from Associate, then Expert and finally to Master.
The first level; Associate, has three certification paths. It has the old MCTS, the MCSA 2008 and the latest MCSA 2012.
Before we continue, it's important to note that you should check the Microsoft site to see if there have been any changes to the requirements, and to see whether exams are still available. Exams usually expires when mainstream support for the product ends.
The MCSA 2008 (Microsoft Certified Solutions Associate) looks at configuring and supporting an Active Directory environment using Windows Server 2008. To gain this cert, you’ll need to pass the following three exams:
70-640 - Active Directory
70-642 - Network Infrastructure
70-646 - Server Administrator
If you already have an MCSA 2008, you are able to update your cert to the new MCSA 2012 in just four days by sitting the 70-417 exam which is available until the 31st of July 2014. This is twice as fast as taking the full MCSA 2012 course and saves the need to start again from the beginning.
 Microsoft Certified Solutions Associate 2012 is aimed at supporting Windows Server 2012 and SQL Server. Like MCSA 2008, you will need to complete three exams in order to gain the certification.
Microsoft Certified Solutions Associate 2012 is aimed at supporting Windows Server 2012 and SQL Server. Like MCSA 2008, you will need to complete three exams in order to gain the certification.
70-410 - Installing and Configuring Windows Server 2012
70-411 - Administering Windows Server 2012
70-412 - Configuring Advanced Windows Server 2012 Services
70-461 - Installing and Configuring Windows Server 2012
70-462 - Administering Windows Server 2012
70-463 - Configuring Advanced Windows Server 2012 Services
 This certification is a level up on the pyramid; this is now in the expert level. It retired a long time ago, and some of you might remember it. But it has been brought back… kind of. It used to be called Microsoft Certified Systems Engineer, but is now called Microsoft Certified Solutions Expert, just like what happened to the MCITP and MCSA. Microsoft Certified Solutions Expert looks at solutions based on the current technology at the time. In order for someone to keep an MCSE certification, they will need to recertify as new technology it released.
This certification is a level up on the pyramid; this is now in the expert level. It retired a long time ago, and some of you might remember it. But it has been brought back… kind of. It used to be called Microsoft Certified Systems Engineer, but is now called Microsoft Certified Solutions Expert, just like what happened to the MCITP and MCSA. Microsoft Certified Solutions Expert looks at solutions based on the current technology at the time. In order for someone to keep an MCSE certification, they will need to recertify as new technology it released.
There are four certification paths for MCSE:
In order to get these certifications, you’ll need to pass the following exams:
70-415 – Implementing a Desktop Infrastructure
70-416 – Implementing Desktop Application Environments
70-413 – Designing and Implementing a Server Infrastructure
70-414 – Implementing an Advanced Server Infrastructure
70-246 – Configuring and Deploying a Private Cloud with System Center 2012
70-247 – Monitoring and Operating a Private Cloud with System Center 2012
70-461 – Querying Microsoft SQL Server 2012
70-462 – Administering a Microsoft SQL Server 2012 Database
70-463 – Implementing Data Warehouses with Microsoft SQL Server 2012
MCSM (Microsoft Certified Solutions Master)
The next level is Master. This is the hardest level to achieve. Professionals at this level have an MCSM – Microsoft Certified Solutions Master. In order to get this certification, you’ll need to complete the relevant certification for that area. But even when that is complete, you’ll need to submit an application to Microsoft for them to approve it. It must show that you have relevant experience and expertise to be awarded this certification. It’s not easy…
The below certifications are the older Microsoft certs which almost all have expiry dates.
This was most common starting point on the Microsoft certification path. Most of the current MCTS exams are due to expire soon. Depending on the certification, you will need to take one to three exams in order to pass. Currently there are 20 different technologies, and it has been said that no new MCTS certifications will be released.
The MCITP certification is what the MCSE is now; the expert level. It is aimed at IT professionals who are responsible for administering the network at a server level. But, currently almost all MCITP certifications except Exchange, Sharepoint and Lync have expiry dates of July 31 2013. It has 15 different certifications. In order to get one of these certifications, you’ll need to pass anywhere from two to five exams. If you have any of the certifications below, you will be able to upgrade them to the new MSCA Server 2012 by taking the 70-417 exam. This is the same exam needed to upgrade your MCSA 2008 to MCSA 2012.
MCITP: Virtualization Administrator
MCITP: Enterprise Desktop Administrator
MCITP: Lync Server Administrator
MCITP: Sharepoint Administrator
MCITP: Enterprise Messaging Administrator
It is important to try and move to the Associate level MCSA 2012 certification as it is the most up to date Microsoft certification and will provide a foundation for your IT career with a stepping stone to the next level: Expert.
Good luck on your chosen certification path.
About the Author:
Julian writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself. Julian is the companies Digital Marketer.
 'Hacktober' lasts the entire 31 days of the month, and has a number of simulated security threats. The security threats includes attacks to employee computers to see if they fall victim to the attack and to see who identifies and reports the issue.
'Hacktober' lasts the entire 31 days of the month, and has a number of simulated security threats. The security threats includes attacks to employee computers to see if they fall victim to the attack and to see who identifies and reports the issue.