الأحد، 31 أغسطس 2014
Why Americans are watching less TV every passing year . Chart of the day
According to the latest Marketing charts, data . TV viewing trends among 8 to 24 age group has been compared .Nielsen’s most recent study indicates that Americans aged 18-24 watched a weekly average of a little less than 22 hours of traditional TV during Q1 2014. That was a 95-minute drop-off from Q1 2013, which in turn had been down by 80 minutes from the year before. In fact, in the space of 3 years, Q1 TV viewing by 18-24-year-olds dropped by a little more than 4-and-a-half hours per week.
That’s a substantial amount, equivalent to roughly 40 minutes per day. In percentage terms, traditional TV viewing among 18-24-year-olds in Q1 2014 was down by almost 7% year-over-year. Between Q1 2011 and Q1 2014, weekly viewing fell by almost 18%, a sizable figure.
That’s a substantial amount, equivalent to roughly 40 minutes per day. In percentage terms, traditional TV viewing among 18-24-year-olds in Q1 2014 was down by almost 7% year-over-year. Between Q1 2011 and Q1 2014, weekly viewing fell by almost 18%, a sizable figure.
Brand Advertising Spends : Paid vs Owned and Earned Media
According to the latest Transparency Market Research published new "Mobile Content Market - Global And U.S. Industry Analysis, Size, Share, Trends And Forecasts 2011 - 2017" market research report show the overall value of the mobile content market as well as the value of the mobile games market in 2011
السبت، 30 أغسطس 2014
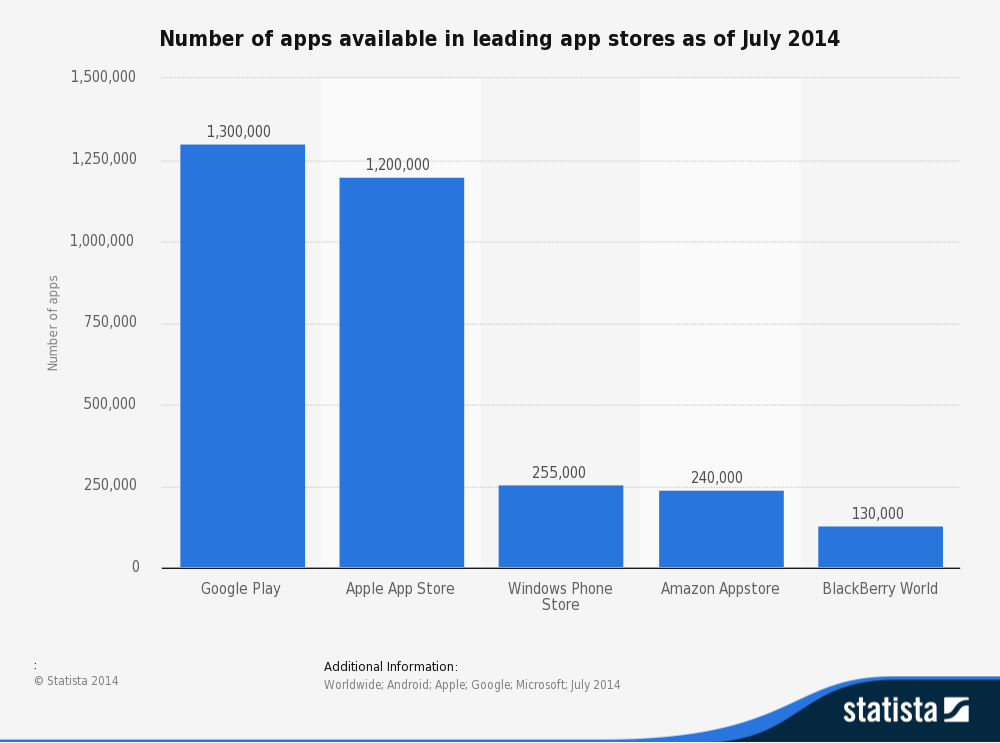
Google Play Pips App Store by one million.
The Biggest Blockbuster iPhone Quarters since its launch : 2007 -2014,volumes grew 8 times since 2007
The Biggest iPhone sales Curve:When did Apple sell the highest number of iPhones
During the last 7years of iPhones existenceNotice the importance of the quarters Q1 2012 , Q1 2013 and Q1, 2014 . These were Apple's biggest iPhone sales blockbusters quarters which saw highest sales volume .These 3 quarters was among the top quarters in the last seven years,when its sales were highest .
If you compare the skyscrapers in the above chart in the 7 years " of iphone sales .. the volume of iphones sold during its first year and second year ( 2007 and 2008 ) have grown 8 times in a 7 year span ...( 2013 AND 2014)
Sales of the iPhone have risen strongly over the years, from around 1.4 million iPhones sold in 2007 to more than 150 million units worldwide in 2013. In total, Apple has sold more than 400 million new iPhones from 2007 to 2013 all around the world. From 2010 to 2013, Apple has held a market share between 13 and 23 percent within the new smartphone sales segment worldwide
الجمعة، 29 أغسطس 2014
Malicious Advertisements Found on Java.com, Other High-Profile Sites
A New York-based online ad network company AppNexus, that provides a platform specializing in real-time online advertising, has again been spotted as the origin of a recent "malvertising" campaign that makes use of the Angler Exploit Kit to redirect visitors to malicious websites hosting the Asprox malware.
AppNexus servers process 16 billion ad buys per day, making it the biggest reach on
الخميس، 28 أغسطس 2014
Microsoft Fixes Faulty Patch Update that Caused Windows 'Blue Screens of Death'
Microsoft today reissued a security update for Windows to the faulty update that previously caused PCs to suffer Blue Screens of Death (BSoD).
The new security update comes almost two weeks after reports emerged that the dodgy update crippled users’ computers with the infamous “Blue Screens of Death.” The company later advised people to uninstall the update, but now it has fixed the issue.
Popular Hackforums Website Defaced by Egyptian Hacker
Hackforums - one of the popular hacking forum in the world - has been hacked and defaced by the famous Egyptian hacker with the online handle Eg-R1z.
HackForums is popular among both whitehats and blackhats. On one end of the spectrum, HackForums helps over 110,000 hacking community members to remove dangerous malware off of their computers, as well as promotes research and learning of
التسميات:
Defacement,
download hacking tools,
Egyptian Hacker,
Hackforums,
hacking forum,
hacking news,
underground forums,
website Defaced
الأربعاء، 27 أغسطس 2014
HardCoded Backdoor Found in China-made Netis, Netcore Routers
Routers manufactured and sold by Chinese security vendor have a hard-coded password that leaves users with a wide-open backdoor that could easily be exploited by attackers to monitor the Internet traffic.
The routers are sold under the brand name Netcore in China, and Netis in other parts of the world, including South Korea, Taiwan, Israel and United States.
According to Trend Micro,
Google Chrome 64-bit Browser Finally Released As a Stable Version
Along with the release of Chrome 37 for Windows, Mac, and Linux, Google today also released a long-awaited 64-bit stable version of its Chrome browser for Windows systems. The company has been working on the 64-bit support for Windows 7 and Windows 8 since June.
Back in June, Google first released Chrome 64-bit only in the browser’s Dev and Canary channels. Then in July, the beta channel
70% of South Korean Population Victimized In Online Gaming Heist
More than half of South Korea's 50 million population aged between 15 and 65 have been affected in a massive data breach, compromising their personal information.
The data breach came to light when 16 individual were arrested following the theft of about 220 million stolen records from a number of online game, ringtone storefronts and movie ticket sites that contains personally
التسميات:
Chinese Hackers,
computer fraud,
Cyber Criminal,
data breach,
game hack,
hacking news,
Korean hacker,
Online Gaming Heist,
South Korea
Stealing Encryption Keys Just by Touching a Laptop
As far sci-fi movies have been entertaining the public, but their ideas have always been a matter of adoption in real life. Just like in any other sci-fi movie, simply touching a laptop can be enough to extract the cryptographic keys used to secure data stored on it.
A team of computer security experts at Tel Aviv University (Israel) has come up with a new potentially much simpler method
Frequently Asked Questions about MCSE: Private Cloud

By Sarah Morgan
The MCSE: Private Cloud certification demonstrates your skills in deploying and managing Microsoft private cloud computing technologies. But what exactly is covered in this certification and what are the benefits of attaining MCSE: Private Cloud? In this post you’ll get all the answers to these and other frequently asked questions about the MCSE: Private Cloud certification.
What’s covered in MCSE: Private Cloud?
Microsoft’s private cloud solutions are built and managed through Windows Server 2012 R2 and System Centre 2012 R2, allowing you to maximise the flexibility of your IT infrastructure.
The MCSE: Private Cloud teaches you the following skills:
- Configuring and deploying the cloud fabric.
- Building the core components necessary for delivering services on the fabric.
- Configuring data centre process automation.
- Allocating resources to a cloud and grant access to a cloud.
- Configuring a PXE server, an update server as well as a software update baseline.
- Configuring Microsoft Server Application Virtualization (App-V).
- Understanding how to monitor clouds using Operations Manager.
- Understanding the tools necessary to extend and customize Operations Manager for cloud environments.
- Setting up, configuring, and integrating the core components of Service Manager into a cloud fabric.
- Configuring a service catalogue, and publishing it to the Self-Service Portal
The MCSE: Private Cloud is ideal for server administrators, network administrators and data centre administrators working with Microsoft technologies. This certification validates their skills in designing, installing and configuring private cloud infrastructures.
Are there any other cloud certifications from Microsoft?
Currently the MCSE: Private Cloud certification is the only strictly cloud-related credential available from Microsoft, however it would not be surprising if there were new ones coming in the next year or two.
How can I get MCSE: Private Cloud certified?
Building your private cloud requires an in-depth understanding of Windows Server 2012 and System Centre 2012. Therefore, as a prerequisite to getting this certification, you need to already hold your MCSA: Windows Server 2012.
Once you have completed the prerequisite certification, you can work towards the MCSE> Private Cloud. This involves passing the following exams:
- Monitoring and Operating a Private Cloud with System Center 2012 Exam 70-246
- Configuring and Deploying a Private Cloud with System Center 2012 Exam 70-247
There’s a great set of resources that will help you with your preparation. If you need exam help, visit the Microsoft Virtual Academy and/or watch the following preparation session from TechEd North America 2014:
If you’re after something more thorough, check out Keith Mayer’s comprehensive guide to building a private cloud in just one month. You’ll find loads of great articles, videos and ebooks here.
What are you waiting for? Leave the world of public clouds behind and build your very own private cloud to ensure that your data stays safe.
About the Author:
Sarah writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself. Sarah has 11 years of experience in the IT industry.
Sarah writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself. Sarah has 11 years of experience in the IT industry.
الثلاثاء، 26 أغسطس 2014
ICREACH — NSA's Secret Google-Like Search Engine for Metadata Analysis
The United States National Security Agency (NSA) is using a massive information sharing platform that allows multiple law enforcement agencies to infiltrate more than 850 billion communications records detailing e-mails, phone calls, instant messages, and phone geolocation, according to the classified documents disclosed by former intelligence contractor Edward Snowden.
The NSA has built
الاثنين، 25 أغسطس 2014
Sony PlayStation Network Taken Down By DDoS Attack
It’s been a bad weekend for Sony Playstation. The entire PlayStation Network was down much of the day after a dedicated distributed denial-of-service (DDoS) attack by online attackers, which left the network inaccessible to users.
It's possible that EVE Online and Guild Wars 2 have also been hit by the attackers. Developers on the EVE Online forums have announced DDoS issues, and many
3 Steps to Master and Create the Art of Scientific Link Bait :
Link Baits are intended to help a website to get " higher number of Back Links within a short period of time . This leads to sudden visibility and increase of traffic ( as more websites across your vertical links back to you.).
This might happen if you have recently updated your page with something really of value in terms of content publication..across your vertical, on your industry
This might be a form of a chart on the latest changing market shares in your industry, infographic on the state of marketshare, or you have published content that " has not been produced elsewhere within that industry and websites that are generally considered to be experts on those topics ( according to google )
What is important that " You actually might not have written " something which did not exist elsewhere, But the important thing is within the list of web sites, which Google spiders continue to crawl and look for more than 200 decisive metrics, you happen to be among the top few sites in that Category
A sites might have great content, better than yours , but if its not indexed as yet.. You will continue to rank well in that " keyword..till the sites are indexed fully
Infographics are not merely examples of link baiting .. Charts/ ebooks /Ads across social media ( text/display or vide ) including Webinar and Podcasts too
الأحد، 24 أغسطس 2014
Targeting Mutual Fund Investors
According to the latest market insights on Mutual Fund Investors the kind of people investing on Mutual Funds has become older as more younger adults enter the stock market via directly buying the shares of the company instead of purchasing through a mutual fund agent
السبت، 23 أغسطس 2014
This day that year : 26th August Celebrity Birthdays
August 26th Celebrity Birthdays
Macaulay Culkin : Actor
Melissa Mcarthy : Actor
David Price : Basketball Player
Mother Teresa: religious and social worker
Cassie Ventura ; Singer
Daniel O Brien : TV Actor)
James Harden : Basketball Player
Neeru Baweja : Bollywood movie actor
Kim Burrel : Singer
Oleg Takrarov : Actor
Keith Allison: Singer
Brian Kelley : Singer
Madhur Bhandarkar : Director
Shirley Mansion : Singer
Chris Burke : TV Actor
Michael Jetter : Movie Actor
Ingrid Bergman : Director
Macaulay Culkin : Actor
Melissa Mcarthy : Actor
David Price : Basketball Player
Mother Teresa: religious and social worker
Cassie Ventura ; Singer
Daniel O Brien : TV Actor)
James Harden : Basketball Player
Neeru Baweja : Bollywood movie actor
Kim Burrel : Singer
Oleg Takrarov : Actor
Keith Allison: Singer
Brian Kelley : Singer
Madhur Bhandarkar : Director
Shirley Mansion : Singer
Chris Burke : TV Actor
Michael Jetter : Movie Actor
Ingrid Bergman : Director
Highest M&A Deals by Investment banks in 2013;
In 2013 Goldman Sachs was the leading bank by the value of managed Merger and Amalgamation deals. In 2013, mergers and acquisitions managed by Goldman Sachs were worth a total of around 604 billion US dollars. The number 2 investment bank in the list was JP Morgan with 563.7 US billion dollars, followed by Morgan Stanley
.
A full-service investment banks usually provide both advisory and financing banking services, as well as sales, market making, and research on a broad array of financial products, including equities, credit, rates, currency, commodities, and their derivatives
. .
Hacking Gmail App with 92 Percent Success Rate
A group of security researchers has successfully discovered a method to hack into six out of seven popular Smartphone apps, including Gmail across all the three platforms - Android, Windows, and iOS operating systems - with shockingly high success rate of up to 92 percent.
Computer scientists the University of California Riverside Bourns College of Engineering and the University of
التسميات:
Android,
Android hacking,
Chase Bank hacking,
gmail hacking,
gmail hacking tool,
hacking news,
iOS hacking,
malicious apps,
mobile apps,
shared-memory side channel
الجمعة، 22 أغسطس 2014
Facebook Awards $50,000 Under Its New 'Internet Defense Prize' Program
Along with a dream to make Internet access available to everyone across the world, Facebook founder Mark Zuckerberg is working to make the Internet a more secure place as well.
Till now, a number of large technology companies have bug bounty programs to reward researchers and cyber enthusiast who contribute in the security of Internet by finding out security holes in software or web
Remote Attack Could Format Your Pebble Smartwatch Easily
Pebble, a wristwatch that can connect to your phone - both iOS and Android - and interact with apps, has a hard-coded vulnerability that allows a remote attacker to destroy your Smartwatch completely.
Pebble Smartwatch, developed and released by Pebble Technology Corporation in 2013, is considered as one of the most popular SmartWatches that had become the most funded project in the
التسميات:
Android,
denial-of-service attacks,
dos attack,
hacking news,
hacking WhatsApp,
Pebble Smartwatch,
smartwatch hacking,
The Hackers Conference,
Vulnerability
5 ways to prepare for your CompTIA A+ Exams you didn't consider

By Alex Bennett
Many an IT professional’s career has been built upon the solid foundation of knowledge that comes from achieving CompTIA’s A+ qualification. In fact, over 925,000people around the world have achieved the A+ over the past 20 years.
Several major brands – like Dell, HP and Lenovo – require that their channel technicians are A+ certified in order to service their products. It is also supported by government branches like the US Department of Defence.
Plus, the skills you’ll pick up from this certification are vendor neutral, making them infinitely useful across your entire career.
The A+ proves you have a good level of knowledge and troubleshooting skills needed to provide capable support to personal computers.
In order to don your A+ badge with pride, you’ll have to pass two exams:
CompTIAA+ Essentials, exam code 220-801
o Which covers basic computer concepts, PC hardware, basic networking, soft skills and safety
CompTIAA+ Practical Application, exam code 220-802
o Which covers operating systems, security, mobile devices and troubleshooting
Each exam takes 90 minutes and you can expect to complete around 90 questions per test.
But, just because it’s an entry level certification, don’t think it’s a push-over. Perhaps the worst thing you can do is have misplaced confidence, if you don’t prepare for the exam, there’s a good chance you won’t pass.
So if you’re gearing up to take A+ or your 3 year A+ recertification is coming up – here are some ways to prepare you might not have considered:
1. Dive into your desktop
The A+ assesses your knowledge of personal computer components like: motherboards, processors, memory, storage devices, power supplies, laptops and portable devices.
This focus on computer hardware gives you the perfect opportunity get your hands dirty. Revision doesn’t have to just involve stooping over a study book – exploring real hardware can be a valuable, effective and enjoyable method of studying for this section of the A+.
Chances are you probably own a desktop computer, or at least have one somewhere in your house. If not, ask around for an old computer (it doesn’t have to work, it just has to be fairly intact). Get yourself a screwdriver and start dismantling the machine – don’t go overboard though, if you don’t know how to reassemble the hardware - but still need to use the PC- don’t take it apart to begin with.
Here’s a quick guideon how to disassemble your PC.
If you can find an old dilapidated desktop computer or printer, dismantle it as much as you can. The more familiar you are with the inner-workings of computers, laptops and printers – the better prepared for the exam you’ll be.
Even if you can’t dismantle the whole computer, you’ll still be able to identify the components you know and research the ones you can’t recognise. It’s a fun diversion to typical revision and will definitely translate into a better exam score.
2. Make friends with Professor Messer
Check out Professor Messer’s CompTIA A+ guide on YouTube, you won’t be disappointed. These quality, in-depth videos are an absolutely brilliant study resource.
Oh, and they’re all totally free. You won’t need to register either – everything is uploaded full-length on YouTube. You won’t have to give over any of your time or money.
Each video segment is around 20 minutes, enough time for a very in-depth lecture. Grab your notepad and a cup of coffee and settle in. It may take several viewings to really embed the stuff in your brain but once again, it’s a great, more passive alternative to poring over a textbook all day.
3. Don’t trip up on the legacy questions
You’ll undoubtedly find some topics in the A+ exam harder than others. That being said, the legacy/older information is sometimes neglected and definitely could trip up students who aren’t prepared for it.
The CompTIA A+ does still cover outdated hardware. You could get a question on floppy disks (yes, really). It’s unbelievable but it could happen, don’t just gloss over these sections when revising – you never know which parts of the curriculum will show up in the exams.
4. Know the question style
You can expect 3 distinct question types on the two exams:
Multiple choice with single answer – you will be required to select a single answer from a range of options (generally 4-5) by clicking a radio button.
Multiple choice with multiple answers – you’ll have to select a range of options from a given set to get the mark.
Fill in the blank - select the missing text to complete the sentence (essentially a multiple choice question in a different format).
5. Check out Firebrand Learn
We’ve uploaded our entire A+ courseware on Firebrand Learn. It’s all totally free and you don’t even have to register to access it. If you’re looking for a comprehensive catalogue of everything you need to learn, this is your best bet.
Plus, as this courseware makes up part of Firebrand Training’s A+ syllabus – get trained with Firebrand and you’ll be more than prepared to score an A+ on the A+ (sorry).
About the Author:
Alex writes for Firebrand Training on IT and certification related topics. He also serves as the in-house designer at Firebrand's Regent Street office.
Alex writes for Firebrand Training on IT and certification related topics. He also serves as the in-house designer at Firebrand's Regent Street office.
Samsung To Pay $2.3 Million Fine for Deceiving the U.S. Government
The United States division of Samsung has been charged with deceiving the US government into believing that several of its products met the necessary US government policies, resulting in the US government buying unauthorised Chinese-made electronics.
The South Korean electronics giant has agreed to pay the Government $2.3 million in fines to settle the charges of violating trade agreements
الخميس، 21 أغسطس 2014
The Economics of Chinese takeover of America's 2nd largest Movie Chain

You will find more statistics at Statista
By purchasing America's second largest cinema chain, Dalian Wanda Group now owns American's 2nd largest movie theater the AMC Entertainment group foreign takeover yet by a private Chinese company. However the fact remains that why would a Chinese company be interested in a market like US where growth has been flat and for all the hype " movie making business is not really a big profit churner , as the financial risks are too high , the number of blockbuster hits coming out of US has been nothing to boast off
However these much more to this that " financial profits". Its like an apple iphone, which has become an American icon world over, ever mind the factories where its churned out are at Taiwan and China ..Taking over US Movie Theatres in US, by Chinese is akin to the same thing
Dalian Wanda's takeover is a kind of " Cultural Perestroika " which Chinese would use as a platform for increasing its own film industry " with a large US audience" ( remember Hidden Dragon and Crouching Tiger
Just as Chinese goods have flooded American markets. China wishes to expand its own cultural horizon, along with markets with deep pockets and keep its rapidly growing economy hungry for more .
The tech that gets you (A-level) results

By Alex Bennett
Thursday 14th August marked the day students across the country received their A-level results. But it wasn’t just stressful for the students - take a moment to appreciate the titanic task of UCAS’ IT team working behind the scenes.
The Universities and Colleges Admissions Service (known to us as UCAS) is responsible for managing all university and college applications. It processes over 650,000 applications a year with the service peaking massively in mid-August.
And this time last week, UCAS sprang into action for what was undoubtedly one formidable working day.
Comprised of about 20 people, UCAS’ Joint Operations Centre (JOC) features the organisation’s IT director, systems operations staff, architects and workers from suppliers such as Amazon, Microsoft and Oracle.
The JOC works with operational intelligence provided by machine data indexer, Splunk. Following a migration to the cloud, UCAS has been using Splunk to monitor its IT infrastructure (the migration actually won a Computer Weekly User Award).
Before the introduction of this cutting-edge tech, UCAS was faced with the monumental challenge of searching and visualising a massive volume of machine-generated data. Now, with the introduction of Splunk, UCAS can troubleshoot, manage performance and use analytics to support the IT team.
Ensuring an uninhibited service is paramount. No more so than during Thursday’s ultra-peak time, where thousands of students will be simultaneously accessing information through UCAS’ Track portal.
Splunk Enterprise is deployed across 40 servers and about 70 log sources, which are in turn deployed through Amazon Web Services. By indexing, searching, alerting and reporting on data from across UCAS’ entire infrastructure, Splunk provides the JOC with a series of visualisations of their performance, key operational metrics and the queries they are running.
Keeping the system operational is a considerable challenge – last year saw the Track system, hosted on the Microsoft Azure cloud service, dealing with more than 180 logins per second.
The operation is based in Cheltenham, where 10 gigantic screens monitor the entire system. Two of these screens are devoted to Splunk which in turn has 10 dashboards created through queries in the software. Some dashboards are devoted to tracking the response time on an applicant enquiry whilst others display response time over a 24-hour period.
Like the phoenix, ‘UCAS lives and dies on one day a year,’ states Peter Raymond, Enterprise IT Architect at UCAS.
Chances are, it’s wasn’t just students experiencing sleepless nights last week.
About the Author:
Alex writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself.
Alex writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself.
Here's why every organisation needs an ethical hacker

By Sarah Morgan
Protecting sensitive information should be every business’ number one priority, especially when high-profile data breaches are becoming increasingly common. But what can organisations do when cyber-attacks become more and more sophisticated and hackers are able to steal 1.2 billion username and password combinations? Well, as the well-known adage says “the best defence is a good offence”, so it’s time to recruit your in-house (ethical) hacker, if you want to keep your data safe.
Ethical Hacking from a company’s perspective
Every organisation is different; with different goals and objectives, different ways of operating, different websites, and of course different potential vulnerabilities.
By definition “an ethical hacker is a computer and network expert who attacks a security system on behalf of its owners, seeking vulnerabilities that a malicious hacker could exploit.” The process of performing such attacks is called penetration testing and it allows companies to remediate critical vulnerabilities.
Tests like this are quite costly, normally starting from around £2,000 for a small company and increasing in proportion with the size of the organisation. These expenses are often hard to justify, especially for those who do not understand the magnitude of potential damages caused by a security breach.
Do you know the average cost of an attack? According to IDG Research a single hack can cost your small or medium sized business up to £600,000 before mitigation even begins. Not to mention the damage to brand reputation.
Photo courtesy of chanpipat/Freedigitalphotos.net
Hire a hacker to protect you
It’s better to be safe than sorry, now is the time to get an ethical hacker on board. But bear in mind that penetration testing is sensitive work and you need to be confident about who you are dealing with.
A Certified Ethical Hacker (CEH) is an expert in the fields of penetration testing, as well as everyday network and application security. They will be able to perform session hijacks, SQL injections, mobile platform hacks and other critical tasks to discover your network’s weak spots, including physical security, such as access to server rooms.
Tools, trick and techniques for future ethical hackers
Do you think your organisation could benefit from having an ethical hacker on board? Then why hire someone external, develop your own ethical hackers instead. The CEH course will teach your employee(s) the most up-to-date techniques to hack into the latest operating systems, such as Windows 8.1. They will learn practical skills, enabling them to thoroughly test your systems and ensure that vulnerabilities are patched.
Retrieving malware directly from hosting locations, tracking devices through Wi-Fi or Bluetooth or improving penetration test effectiveness – these are all possible with the help of some of these new tools, introduced at Black Hat USA 2014.
Are you interested in more of the latest methods and ways to protect against hackers? Don’t miss out on the European edition of Black Hat 2014, this October in Amsterdam.
Will you wait until it’s too late?
According to Katy Reynolds, a security consultant for Context Information Security, “there is a tendency for companies to bury their heads in the sand as no one wants to believe they are vulnerable to hackers or identify that money must be spent to fix potential problems,” which often brings devastating results.
What will your company do?
About the Author:
Sarah writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself. Sarah has 11 years of experience in the IT industry.
Sarah writes for Firebrand Training on a number of IT related topics. This includes exams, training, certification trends, project management, certification, careers advice and the industry itself. Sarah has 11 years of experience in the IT industry.
Hacking Traffic Lights is Amazingly Really Easy
Hacking Internet of Things (IoTs) have become an amazing practice for cyber criminals out there, but messing with Traffic lights would be something more crazy for them.
The hacking scenes in hollywood movies has just been a source of entertainment for the technology industry, like we've seen traffic lights hacked in Die Hard and The Italian Job, but these movies always inspire hackers to perform
The hacking scenes in hollywood movies has just been a source of entertainment for the technology industry, like we've seen traffic lights hacked in Die Hard and The Italian Job, but these movies always inspire hackers to perform
MasterCard to Double its Transactions to 42billion on the back on 4 new co-branding Launch
Credit card giant MasterCard, the second largest payments network in the U.S has been outmaneuvering its rivals and outbidding the markets this year in 2014 ,led by surging transaction volumes in US and as well as non US markets
- The strong performance was also reflected by a nearly 14% growth in revenues in the first half of 2014 compared to the previous year.
- MasterCard in 2013 processed over 38 billion transactions and in 2014 April it has already processed over 20 billion transactions. Online Stock Research and consultancy firm Trefis is projecting an excess of 41 of billion transactions by MasterCard ending this year in 2014
- Though the numbers look too big to be achieved. Recently MasterCard has drew and slew up many plans that could help achieve its ambitious growth numbers .Among them include
- It has created co-branded card partnerships with retail giants Target (formerly partnered with rival visa on co-branded cards) and Wal-Mart which dumped Discover to sign on with MasterCard),
- Launched an partnership with Amazon in Japan on a co-branded card.
- MasterCard also expanding the Wal-Mart co-branded card beyond ond the U.S. to Latin American markets
- MasterCard’s recent agreement with the Middle Easts largest retail brands Landmark Group, will provide MasterCard with access to more than 6 million new customers
- MasterCard, originally known as Interbank/Master Charge, was created by several California banks as a competitor to theBankAmericard issued by Bank of America, which later became the Visa credit card issued by Visa Inc In the U.S., which alone contributes 40% of total revenues and is a highly penetrated market
الأربعاء، 20 أغسطس 2014
Customizing a car within 140 Characters:Acura luxury Sedans to be Twit-delivered
Customizing Your car online via a tweet .Digiday has posted a tweet, which shows ' what might be actually the first such case of using twitter to customize your 2015 TLX performance luxury sedan within a tweet
Acura, which is the luxury division of Honda Motor Corp has been showcasing a launch of its digital campaign whereby yo can customize is trumpeting the launch of the by letting you create a customized car, within Twitter in 4 steps
Step 1 " Choose the Engine Type 206 HP 4 cylinder or 290 Hp V6
Step 2 Choose the drive train steer type
Step 3 : Chose the Color of yourAcura
Step 4 : Select the 2015 Acura model TLX and retweet to your friends
Acura, which is the luxury division of Honda Motor Corp has been showcasing a launch of its digital campaign whereby yo can customize is trumpeting the launch of the by letting you create a customized car, within Twitter in 4 steps
Step 1 " Choose the Engine Type 206 HP 4 cylinder or 290 Hp V6
Step 2 Choose the drive train steer type
Step 3 : Chose the Color of yourAcura
Step 4 : Select the 2015 Acura model TLX and retweet to your friends
Acura is the luxury vehicle division of Japanese automaker Honda Motor Company. The brand has been available in the United States and Canada since March 1986, marketing luxury, performance, and high-performance vehicles.
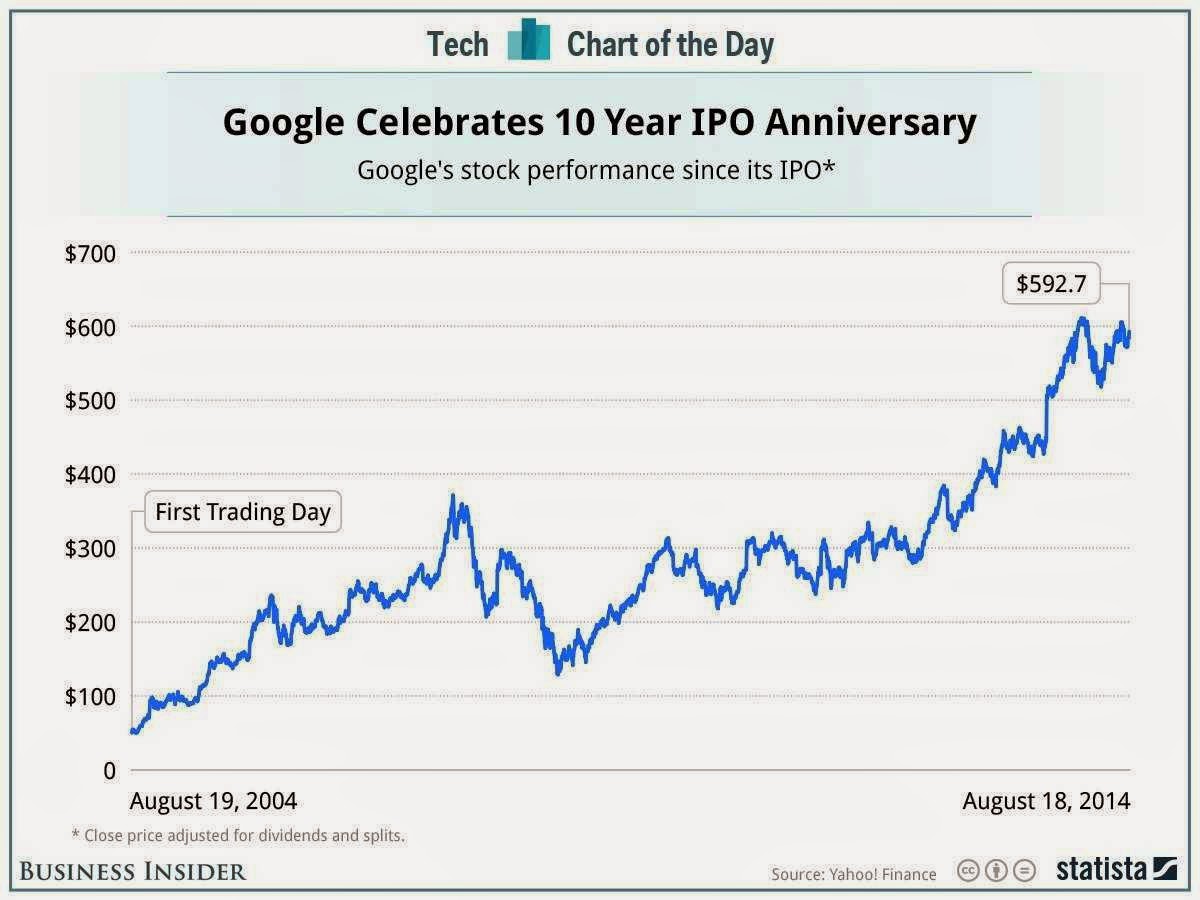
Google IPO Debut :Completes a Decade and Counting
According to For Google this week had been an historic one has this 18th August, 2014 had been 10 years since Google debuted its IPO. While Google has seen many ups and downs, and at that time no none could have thought " Google would be powering their smartphones via the Mobile OS Android.. But the fact remains that 10 years in an technology industry , Google has mellowed ,made money, and made a lot of enemies ( Microsoft, Apple )
However there has been many anecdotes and behind the scenes on the run up to the IPO..which have been republished- The value of the shares Google decided to offer was a nerdy little joke: $2,718,281,828 - the first nine decimal places in the irrational number e.t -.
- Google decided that its S-1, a required document that lays out a company's financials and risks and is usually written in legalese, would be written simply and intimately. "Google is not a conventional company," cofounder Larry Page started the letter. "We do not intend to become one.
- A day after the IPO On August 19, 2004 the number of shares outstanding was 172.85 million while the "free float" was 19.60 million (which makes 89% held by insiders)
- Cofounder Sergey Brin didn't even show up for the ringing of the bell on the day of the IPO because he didn't want to take a red-eye flight.
- Larry Page showed up wearing a suit he bought at Macy'sGoogle IPO Debut : A decade and Counting
AlienVault Releases Intrusion Detection Systems (IDS) Best Practices
Network security practitioners rely heavily on intrusion detection systems (IDS) to identify malicious activity on their networks by examining network traffic in real time. IDS are available in Network (NIDS) and Host (HIDS) forms, as well as for Wireless (WIDS). Host IDS is installed via an agent on the system you are monitoring and analyzes system behavior and configuration status. Network
'AdThief' Chinese Malware Infects Over 75,000 Jailbroken iOS devices
If you have jailbroken your iPhone, iPad, or iPod touch and have downloaded pirated tweaks from pirated repositories, then you may be infected by “AdThief” malware, a Chinese malware that is now installed on more than 75,000 iPhone devices.
According to a recent research paper published on Virus Bulletin by the Security Researcher Axelle Apvrille, the malware, also known as "spad," was
How Many Degrees of Digital Screens Separate us
Amidst the growing Proliferation of screens at work and at our personal lives.. Its kind of interesting to see " How much time we spent starting or working on the screen How much do we use screens as modern day " factory tools ( industrial revolution ). How much of technology has crept into our lives .. and how much pixels of screen has : been added to our layers" to technological marvel
This chart shows how we compare across nations when it comes to spending time surrounded by screens. According to a survey conducted by Ipsos among more than 16,000 consumers from 20 countries, 60% of consumers feel like they are constantly looking at screen these days.
This chart shows how we compare across nations when it comes to spending time surrounded by screens. According to a survey conducted by Ipsos among more than 16,000 consumers from 20 countries, 60% of consumers feel like they are constantly looking at screen these days.
الاشتراك في:
الرسائل (Atom)

.png)



.png)











.jpg)
